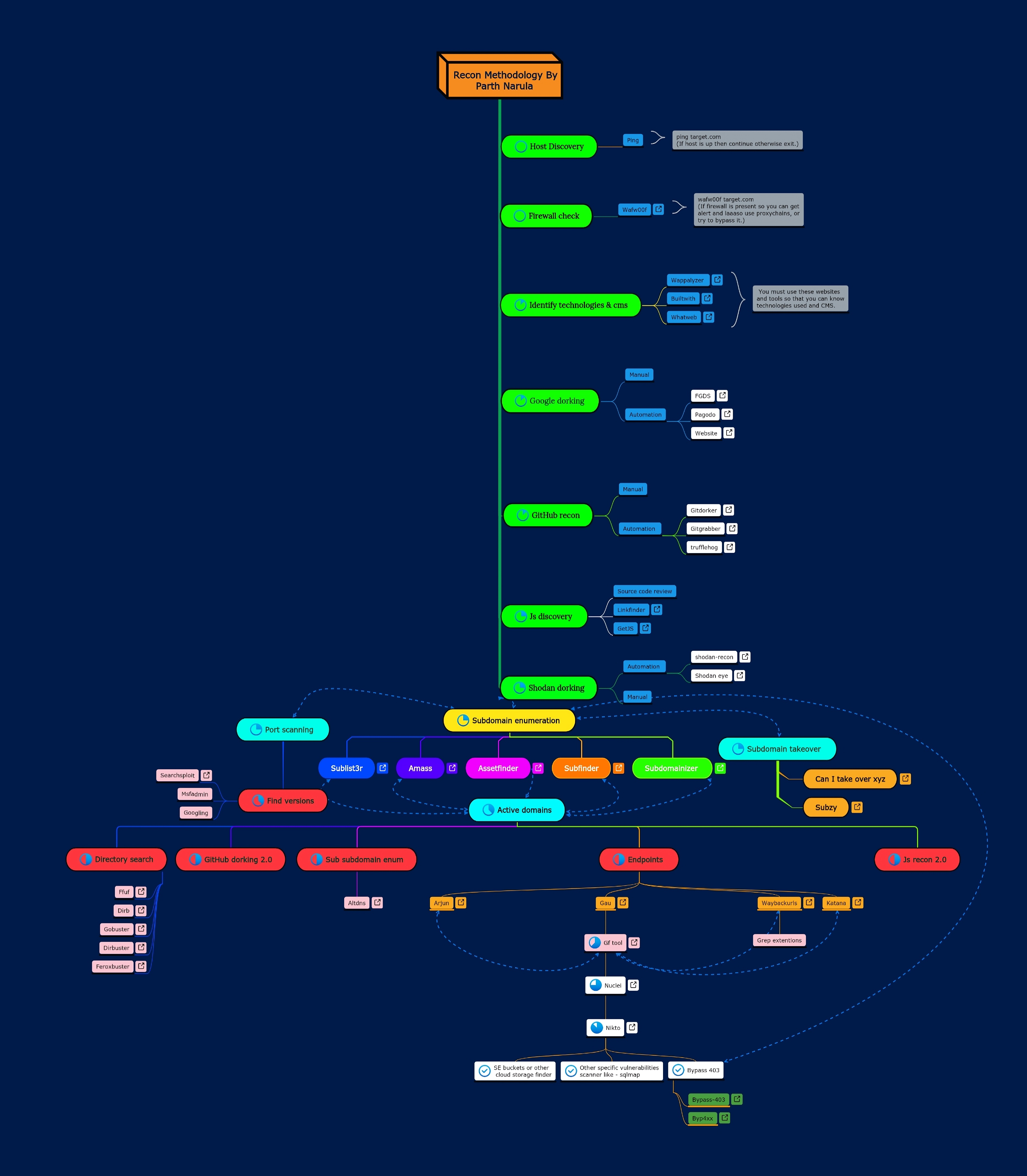
Research On Recon
Hello guys welcome to recon page, Here we will provide you a very deep recon methodology that will surely help you in increasing you attack surface. You can cick on image and download it from the drive link.
Steps For Recon
- Host Discovery You must check weather the host is up or down before starting recon. Simple utility for that is ping.
- Firewall Check You must check firewall like cloudflare, cloudfront to later on try for bypasses related to it. Most popular tool for that is wafw00f.
- CMS Detection You must check the which CMS (Content Management System) like WordPress, Joomla, etc to do possible attacks/scans related to it.
- DNS Recon You should perform DNS Enum/Recon to gather its information, It may discover something. Tools that often help are Dnsrecon, Dnsenum, etc.
- Basic Info You must gather other basic info like its past screenshot from web.archive.org, its seeds, whois dnsdumpster.com, whatweb, theharvester, maltego, spiderfoot, etc.
- Google Dorking You have to perform google dorking from both manual and automation. Tools that can help are FGDS, Pagodo, GHDB, etc.
- Github Dorking You should perform github recon from both automation and manual approach so you can get some leaked information. Tools that can be used are gitdorker, gitgrabber, etc.
- JS Discovery You must check the JS files it can leak some sensitive URL or credentials. Tools are subJS, getJS, Linkfinder, etc.
- Shodan Dorking You must check the IP and Domain on shodan it can give us some hidden IP's or secret info related to target and you should try manual approach for this. Tools for helping you shodan-eye, shodan-recon, etc.
- Subdomain Enum You must grab all the subdomains to increase your attack surface area and your scope, you may find hidden subdomain. Tools like sublist3r, subfinder, assetfinder, amass, etc.
- Network Scanning You can then perform network scanning on those subdomains or on particular domai to see services running, open ports, etc info. Nmap and masscan are useful tool.
- Sub Takeover You can then try to takeover 404 subdomain with a CNAME record and if you dir so boom it's a vulnerability. Tools that may help are sybzy, can-i-takeover-xyz, nuclei, etc.
- Active Subdomains You have to filter active and working subdomains to do your futher attacks. Can use httpx or httprobe tool.
- Sub Sub Enum You should check for sub sub domain to increase the attack surface and find unknown domains. Useful tool is altdns.
- Dir Busting You must check for hidden directories, files and pages to get sensitive info. Popular tools are ffuf, gobuster, dirbuster, dirb, etc.
- Grabing Params You have to grab the paramaters and endpoints to check for injections and other vulnerabilities. Tools like gau, waybackurls, katana, etc.
- Vulnerable Params You should grep parameters that may vulnerable to specific vulnerability and put them in one file. gf tool will help.
- Open Buckets You can try to find open buckets sometimes its publically available.
- 403 Bypass You must try to bypass 403 (forebidden) pages with several techniques and methods.
- Vulnerability Scan You can perform vulnerability scanning in background with the help of nuclei, nikto, rapidscan, etc.
- Particular Vul Scan You have to run tools for particular vulnerability like sqlmap for sqli, xsser for xss, tqlmap for ssti, etc.